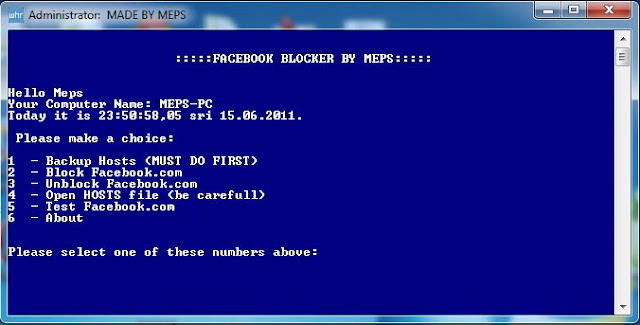
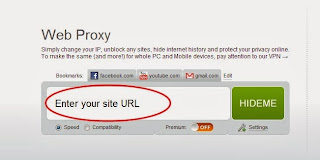
Below is the list of some good proxy site which you can use to surf anonymously on the internet . Even you can use this proxy sites to open block website in school or offices. For example you can use
facebook if it is block at your school or office.
Here is proxy list:--
http://aniscartujo.com/webproxy
http://www.badboysproxy.com
http://www.surfscreened.com
http://www.hagiomusic.info
http://www.greenpips.info
http://urlbrowse.com
http://www.hideipaddress.net
http://www.sneakfilter.com
http://www.browsestealth.com
http://www.sneak1.info
http://proxiesrus.com
http://www.surfindark.com
http://www.navydog.com
http://falsario.com
http://www.proxypit.com
http://www.proxypan.com
http://myspacewebproxy.org/
http://www.allfreehere.info
http://www.takefreely.info
http://autobypass.com
http://www.proxcity.info
http://www.proxyzip.org
http://www.cheekyproxy.com
http://www.eggproxy.com
http://www.theschoolcloak.com
http://www.hidemefast.com
http://browseanywhere.info
http://www.404surf.com
http://www.cloakip.net
http://www.browsedark.com
http://www.dartprox.com
http://www.proxish.com
http://www.surfsneak.com
http://www.surfsneaky.com
http://www.browsehidden.com
http://www.filterhide.com
http://www.browsesneak.com
http://myspaceproxyy.com
http://www.browsesneaky.com
http://www.proxyz.us
http://www.sneakschool.com
http://www.iphide.com
http://www.proogle.info
http://greatproxy.info
http://www.playnsurf.info
http://www.realproxy.info
http://aplusproxy.com
http://www.ecoproxy.com
http://freedom.webtuo.com
http://www.slyuser.com/
http://tenpass.com
http://pawxy.com
http://pawxy.org
http://logu.in